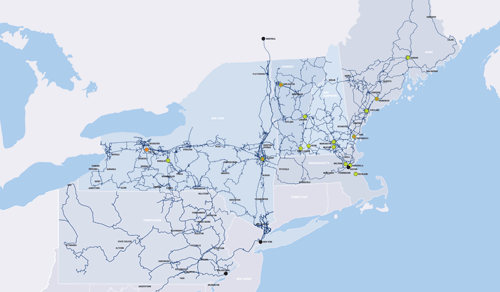
DDoS Protection
400,000 DDoS attacks occur each month. Don’t fall victim.
Nearly 400,000 DDoS attacks happen each month worldwide: That’s the bad news. The good news is with our DDoS Protection and Mitigation solution, you can ensure your organization doesn’t get hit. With the aid of sophisticated algorithms on constant alert for suspicious traffic, we help you block attacks before they can ever materialize.

DDoS Protection & Mitigation Info Sheet
A recent survey of more than 640 IT security and operations professionals revealed that 38% of respondents ranked Distributed Denial-of-Service (DDoS) attacks as their most significant IT security concern.

DDoS – Understanding and Mitigating DDoS Attacks
FirstLight’s DDoS Protection & Mitigation solution can help keep your organization safe while still letting legitimate traffic reach your network.

DDoS Protection – Integrated
The best Internet connectivity is useless if you’ve been hit with a debilitating Distributed Denial of Service (DDoS) attack.
Always-on Alert System
We’re like your own private spy-plane for bugs and bots
Our suspicious activity filters are always on patrol, using algorithms to pinpoint unusual or malicious traffic in real time. Our easy-to-use dashboard keeps you updated and informed with automated notifications, filters, and alerts.
TRAFFIC MAPPING AND TRIAGE
We keep your virtual traffic moving without incident
Our system identifies normal traffic patterns—and sets parameters for pinpoint detection. Our mitigation not only reduces the severity of any attack on you—it also allows for legitimate traffic to reach its intended network destination without delay.
Contact Us
Contact Us Today
You don’t have to go it alone when facing DDoS attacks. We can help. Schedule a demo, speak with our experts, or download our guide to learn more.
Related News and Resources

FirstLight Sponsors Tournament to Benefit Make-A-Wish New Hampshire

How do you communicate in an emergency?

The FirstLight Difference

Unveiling the Future of Networking: Understanding SASE (Secure Access Service Edge)

Bell and FirstLight to offer new high-speed routes with triple redundancy between Secaucus, NJ, Toronto, and Montréal

FirstLight Enhances Its C-Suite with Two Industry Veterans

Aqua Comms Selects FirstLight for Unique Fiber Routes in the Northeast

FirstLight Wins Four Visionary Spotlight Awards

New Area Code Coming to Western New York

FirstLight Appoints Peter Zarrella as CFO

Wirebelt Company of America Chooses FirstLight to Support its New, Energy Efficient Manufacturing Facility

A Beginner’s Guide to Disaster Recovery as a Service

FirstLight Fiber, Inc. Names Jason Campbell as Chief Executive Officer

FirstLight Continues Fiber Network Expansion in Hebron, Sumner

The 2023 Hype Alphabet Soup

New 329 Area Code Coming to the 845 Region in New York

FirstLight Receives 2022 Backup and Disaster Recovery Award from Cloud Computing Magazine

FirstLight Announces Expansion of Residential Broadband in Maine

Performance-Grade Ethernet Explained

The Divide Podcast: How FirstLight is connecting communities with middle-mile fiber

FirstLight Sponsors Tournament to Benefit Make-A-Wish New Hampshire

How do you communicate in an emergency?

The FirstLight Difference

Unveiling the Future of Networking: Understanding SASE (Secure Access Service Edge)

Bell and FirstLight to offer new high-speed routes with triple redundancy between Secaucus, NJ, Toronto, and Montréal

FirstLight Enhances Its C-Suite with Two Industry Veterans

Aqua Comms Selects FirstLight for Unique Fiber Routes in the Northeast

FirstLight Wins Four Visionary Spotlight Awards

New Area Code Coming to Western New York

FirstLight Appoints Peter Zarrella as CFO

Wirebelt Company of America Chooses FirstLight to Support its New, Energy Efficient Manufacturing Facility

A Beginner’s Guide to Disaster Recovery as a Service

FirstLight Fiber, Inc. Names Jason Campbell as Chief Executive Officer

FirstLight Continues Fiber Network Expansion in Hebron, Sumner

The 2023 Hype Alphabet Soup

New 329 Area Code Coming to the 845 Region in New York

FirstLight Receives 2022 Backup and Disaster Recovery Award from Cloud Computing Magazine

FirstLight Announces Expansion of Residential Broadband in Maine

Performance-Grade Ethernet Explained