Overview
Hackers gonna hack. Unfortunately for them we’re on your side.
We get what you’re up against: Malware, DDoS attacks, network breaches—any of these can wreak havoc on your business in a matter of seconds. But not to worry. We’ll implement the perfect combination of technologies and solutions that can prevent — or help you recover from — even the worst incursions.
DNS Protection
When it pours malware, FirstLight’s DNS Protection, powered by Cisco Umbrella, keeps you high and dry
Keeping all the bugs out – without affecting user performance – is a huge challenge. Luckily, FirstLight’s DNS solution helps integrate security policies for users both on and off your network, so nothing from the outside ever passes through. Our security experts can help you set up and implement your solution – and safeguard your organization.
Learn More About DNS Protection

DNS Protection helps protect your users from cyber threats, regardless of their location.
Security Solutions

FirstLight has a full cybersecurity portfolio to help organizations like yours prepare, prevent and recover from cyberattacks that pose a threat to your organization.
Ransomware White Paper
39% of organizations have no plan to protect their data. Learn how to protect your business.
Ransomware Infographic
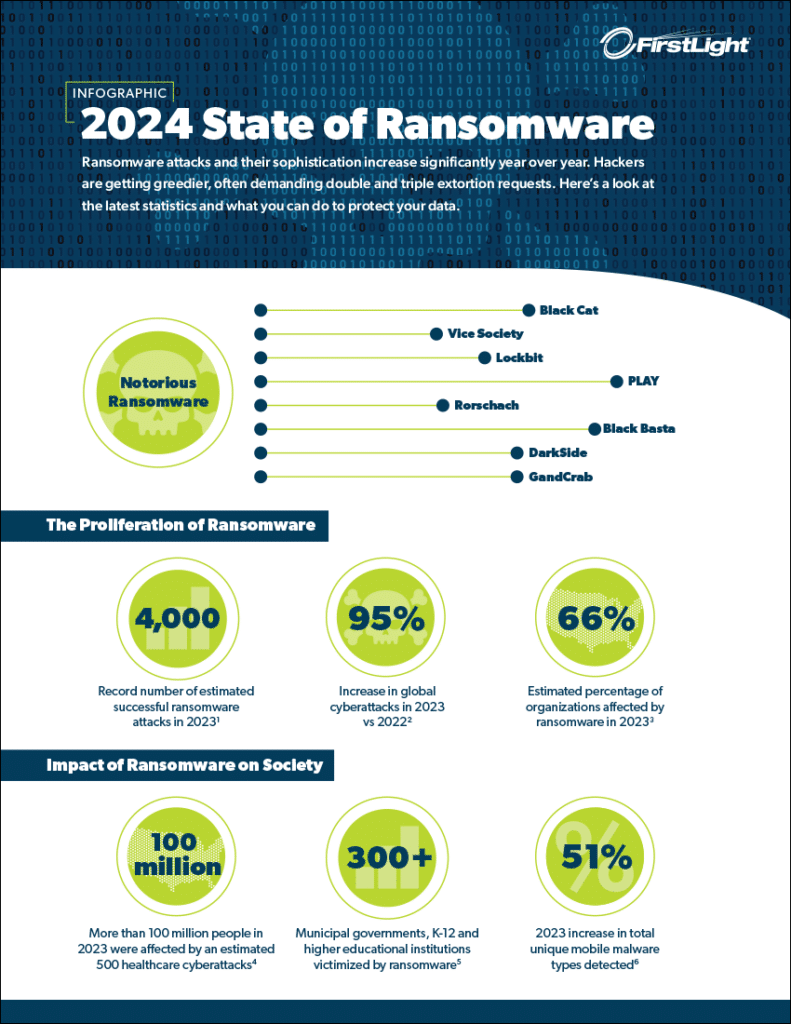
Ransomware is one of the biggest IT threats facing organizations, and it doesn’t appear to be going away anytime soon. Here’s what you need to know to keep your data safe from being taken for ransom.
Cisco Solutions
The right solution for device management
No business has the same, one-size-fits-all needs, which is why we partner with you directly to ensure you’ve got the level of service that suits your needs. As a Cisco Premier Partner, we offer all the hardware and licensing you’ll need to keep your organization shielded from advanced threats. And if you need outside help with deploying or managing any devices – security or otherwise – our team of experts is ready to assist from the jump.

DDoS Protection
Distributed denial of service attacks – denied
Does your Internet provider protect your business from DDoS attacks? We do. Our DDoS protection solution delivers all the safekeeping you need, while keeping a close eye on performance.

DDoS – Understanding and Mitigating DDoS Attacks
FirstLight’s DDoS Protection & Mitigation solution can help keep your organization safe while still letting legitimate traffic reach your network.

DDoS Protection – Integrated
The best Internet connectivity is useless if you’ve been hit with a debilitating Distributed Denial of Service (DDoS) attack.
Cloud Backup
Cloud backup
Whatever the culprit, we’ve got no love for anything that causes you data loss. If you’re hit with ransomware or if your data gets accidently (or maliciously) deleted, then we provide you with a separate, secure offsite backup that you can use to get back on your feet. And if you can’t spare any downtime (and really, who can?), we can couple your cloud backup with our Disaster Recovery solution so that you’re up and running again, almost instantly.
Emergency Alert System
Be Prepared for the Worst-case Scenario
Communication and security are arguably the most important components of success for an organization, and time is of the essence when it comes to both. InformaCast, a powerful mass communication tool, accentuates these components by pushing out important notifications to mobile and on-premises devices. With InformaCast, not a second is spared when an emergency arises. Reach all desired users quickly, easily and with urgency.


Cloud-based Disaster Recovery as a Service
Cloud-based Disaster Recovery as a Service
We work double-time to ensure you never experience any downtime. Our cloud sites are the ideal spaces for replicating your critical workloads. Using our DRaaS solution, you’ll recover from ransomware – or any other cause of downtime – in a flash.
Data Center Security
Data Center
Physical data center security is often overlooked. Our secure facilities and cloud sites are the ideal places to fortify and fireproof your infrastructure and data against all possible threats—both online and offline.