Ransomware has become such a big problem that the U.S. Department of Homeland Security has issued an alert announcing that the Cybersecurity and Infrastructure Security Agency (CISA) has seen an alarming global increase of these attacks.
The New York Times reported that on Christmas day 2019, a Northeastern airport authority experienced a ransomware attack that originated with a third-party management services network and spread to airport servers and backup servers, encrypting administrative files. Hackers demanded a ransom that was reportedly approaching six figures for the decryption key.
Ransomware attacks don’t show any signs of letting up. Instead, they have evolved, making them more difficult to prevent and recover from. However, by taking the correct precautions, your company can help enable a ransomware-free future. The right approach to backup and disaster recovery will help organizations protect their mission-critical data from being encrypted by bad actors.
Here’s a look at 3 strategies that can protect your company from ransomware:
1) Disaster Recovery as a Service (DRaaS)
 Cloud-based disaster recovery is a great way to foil hackers’ plans to extort money from your organization. When backup files are maintained in the cloud, ransomware’s sting is blunted.
Cloud-based disaster recovery is a great way to foil hackers’ plans to extort money from your organization. When backup files are maintained in the cloud, ransomware’s sting is blunted.
Replication is done more frequently, decreasing the amount of data lost and increasing its ability to fail over. The new ransomware attacks aim to delete on-site backup files. If the backup files are off-site in the cloud, that can’t happen.
Data and virtual machines can be replicated to the cloud, increasing availability and ensuring that files are accessible after an attack. After an attack, your company can achieve automatic failover in the cloud. But what happens if the encrypted files from ransomware are replicated into the cloud? A solid disaster recovery and backup solution will offer many points-in-time recovery, allowing you to fail over to the closest moment, just before the ransomware took effect.
Recovery is rapid and complete, meeting even the most demanding recovery point objectives (RPOs) and recovery time objectives (RTOs). When DRaaS is supported by a high-speed network, replication and recovery occur faster and more reliably.
2) The 3-2-1 Rule
To protect your company against ransomware, it’s not enough just to back up your data. If you have a single backup copy of your data stored on-site, your company could still lose information during a ransomware attack.
The 3-2-1 rule for backup recommends that companies make at least 3 copies of mission-critical data. Two of these copies should be kept on different storage media in case one type fails. One of these copies should be stored off-site. This off-site copy could be stored in the cloud.
When organizations follow the 3-2-1 rule, they ensure that at least one copy of company data is out of the reach of a ransomware attack. When your company maintains access to off-site backup files, there is no need to pay a costly ransom.
The 3-2-1-0 Adaptation
Veeam, a FirstLight partner and leading provider of backup and disaster recovery, takes the 3-2-1 rule one step further. Veeam recommends the 3-2-1-0 rule. The 0 stands for “0 errors” during automatic recoverability verification.
The 3-2-1-0 rule can be followed when backing up virtual machines with Veeam. Disaster recovery should provide backup and replication that allows for low RPOs. Data should be recovered not only quickly but also completely to ensure business decisions are made based on current and accurate information.
3) Vigilance With Passwords & Digital Hygiene
 IT managers and administrators — as well as all individuals within an organization — are busier than ever, so repeated changes to passwords are annoying and intrusive. But they’re critically important in helping deter cybercriminals. Don’t get sloppy in using the same password for all your apps, devices, and logins.
IT managers and administrators — as well as all individuals within an organization — are busier than ever, so repeated changes to passwords are annoying and intrusive. But they’re critically important in helping deter cybercriminals. Don’t get sloppy in using the same password for all your apps, devices, and logins.
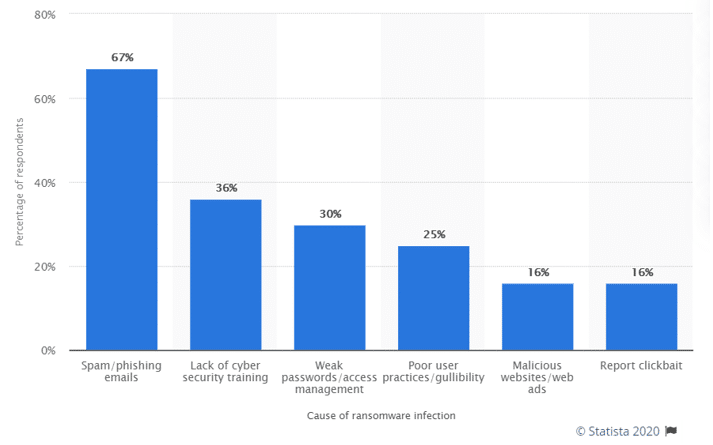
According to a Statista 2019 survey of MSPs worldwide, while ransomware perpetrators may be using the same methods, they are much smarter. A graph representing ransomware infection causes reported by survey respondents revealed that phishing scams are still the most common source of transmitting ransomware (67%), followed by lack of cyber security training (36%), weak passwords/access management (30%), and poor practices/gullibility (25%). Tied for last place at 16% were malicious websites/web ads and report clickbait.
Say Goodbye to Ransomware
When choosing a provider for disaster recovery, companies should keep these 3 ways of defending against a ransomware attack in mind. FirstLight partners with industry-leading data protection and disaster recovery software companies like Zerto and Veeam. Our DRaaS offerings provide a cloud-site for replication and are supported by an extensive high-speed fiber optic network.
FirstLight’s network and DRaaS solution enables RPOs of seconds and RTOs of only minutes.
Get all the information you need to know about cloud-based disaster recovery. Check out FirstLight’s free DRaaS for Dummies guide.